TFTP protocol overview
TFTP known as Trivial File transfer protocol is a simple file transfer protocol with features such as get or put files. Unlike FTP or SFTP which can share files across networks TFTP can only share files over a local network, TFTP is known as Lightweight because it uses UDP(User Datagram Protocol) to transfer files and it has no advanced features such as listing files or listing directories
What problem did TFTP solve?
TFTP, or Trivial File Transfer Protocol, was developed to address specific challenges in network environments, primarily focusing on scenarios where simplicity, speed, and efficiency were crucial.
How does TFTP work?
TFTP operates on a client-server model. The client initiates a connection to the server and sends a request for a file transfer, specifying the filename and the transfer mode (binary or ASCII). The server, upon receiving the request, responds by either sending the requested file or an error message if the file is not found or if there’s another issue.
Visual Representation of TFTP Communication Flow: Client-Server Interaction:
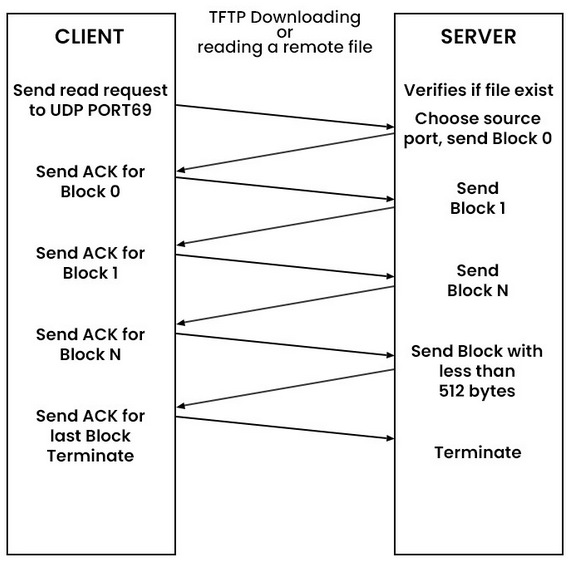
TFTP has 5 Different message types which is used to communicate between client and server. They are:
- RRQ
- WRQ
- DATA
- ACK
- ERROR
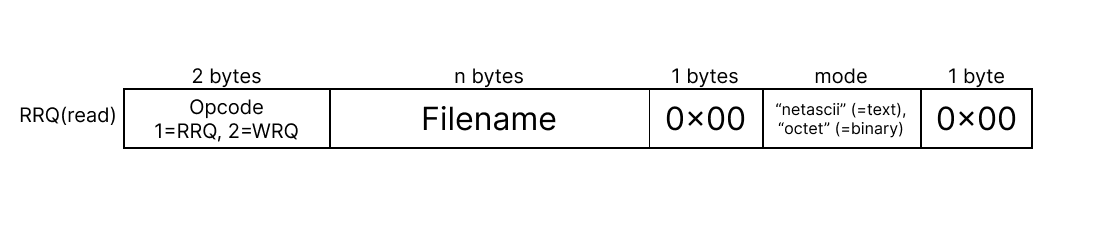
RRQ ( Read Request )
The Read Request message, also known as a GET request, is sent by a TFTP client to request a file transfer from the server to the client. It includes the filename of the desired file and the transfer mode (binary or ASCII). Upon receiving an RRQ, the server responds with a Data packet containing the requested file’s contents or an Error packet if the file is not found or cannot be accessed.
Packet Layout of RRQ message:
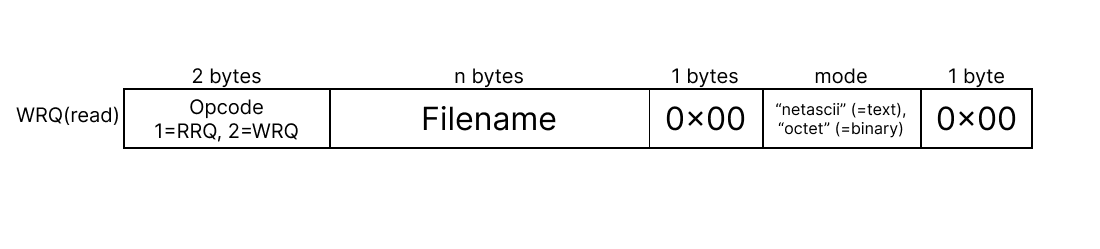
WRQ ( Write Request )
Contrary to RRQ, the Write Request message, or PUT request, is initiated by the client to upload a file to the server. Similar to RRQ, it includes the filename and transfer mode. Upon receiving a WRQ, the server acknowledges the request with an ACK packet, indicating its readiness to receive the file, or responds with an Error packet if the operation cannot be completed.
Packet Layout of WRQ message:
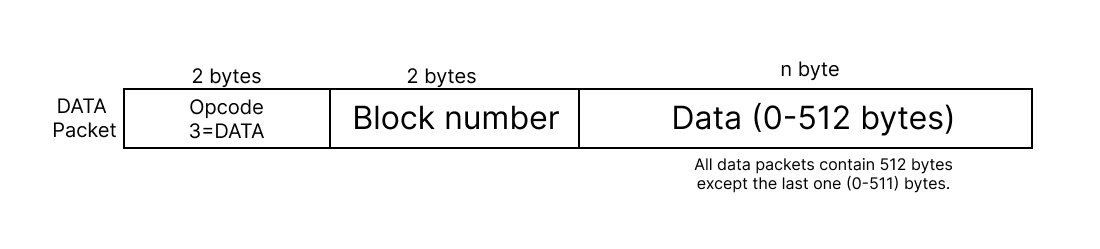
DATA message
The Data packet carries a portion of the file being transferred, typically containing a block of data. Each Data packet includes a block number to facilitate sequential transmission and acknowledgment. After sending a Data packet, the sender awaits an ACK packet from the receiver before transmitting the next block. If the sender doesn’t receive an ACK within a specified timeout period, it retransmits the Data packet.
Packet Layout of DATA message:
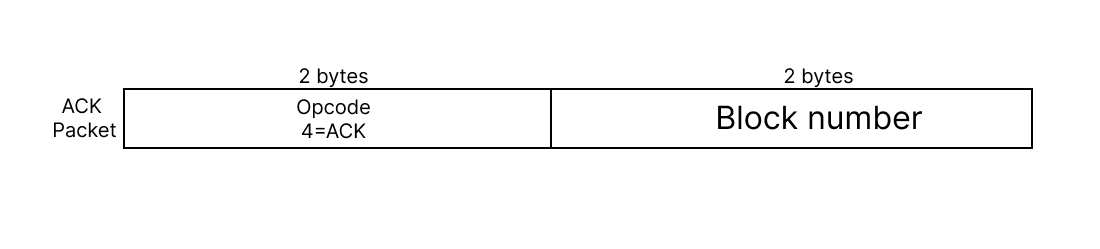
ACK ( Acknowledgment )
Acknowledgment packets, or ACKs, are sent by the receiver to confirm the successful receipt of a Data packet. Each ACK packet contains the block number of the Data packet it acknowledges. Upon receiving an ACK, the sender proceeds to transmit the next block of data. In case of packet loss or corruption, the sender retransmits the Data packet until it receives a valid ACK.
Packet Layout of ACK message:
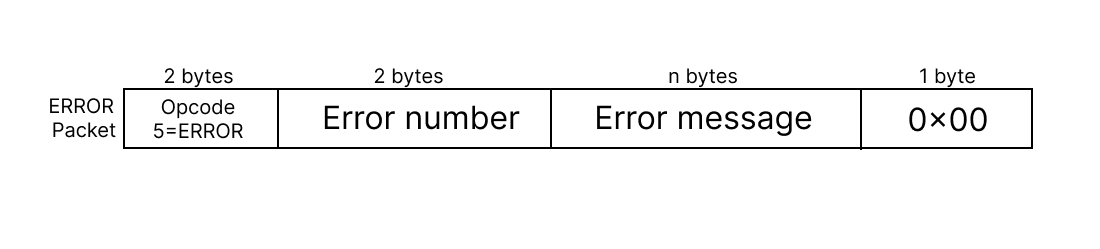
ERROR message
Error packets are generated by either the client or the server to communicate error conditions during a TFTP transaction. An Error packet includes an error code and a textual error message describing the encountered issue. Common error codes include file not found, access violation, disk full, and illegal TFTP operation. Upon receiving an Error packet, the recipient terminates the transaction and may display or log the error message for diagnostic purposes.
Packet Layout of ERROR message:
Advantages of TFTP
-
Simplicity: TFTP’s design is straightforward, with fewer features and commands compared to FTP. This simplicity makes it easier to implement and use, requiring less overhead and fewer resources.
-
Minimalist: TFTP is lightweight, both in terms of its protocol design and its resource requirements. This makes it suitable for embedded systems, such as routers, switches, and other network devices with limited memory and processing power.
-
Fast: Because TFTP operates over UDP, which doesn’t have the connection establishment and teardown overhead of TCP, it can be faster for transferring small files over high-speed networks.
-
Bootstrapping: One of TFTP’s primary use cases is bootstrapping diskless devices, such as network booting of thin clients, diskless workstations, or embedded systems. Its simplicity and low overhead make it ideal for this purpose.
Limitations of TFTP
-
Lack of Authentication: TFTP lacks built-in user authentication mechanisms, which can pose security risks in environments where user access control is essential.
-
Limited Error Handling: TFTP’s error handling capabilities are basic, with error messages providing minimal information about the encountered issue.
-
No Directory Listing: Unlike protocols like FTP or SFTP, TFTP does not support directory listing functionality. Users must manually specify the filenames they want to transfer, which can be cumbersome, especially when dealing with large numbers of files or directories.
-
File Size Limitation: TFTP is not optimized for transferring large files efficiently. Its reliance on UDP and lack of features like file segmentation or resuming transfers mean that transferring large files can be slower and less reliable compared to protocols designed specifically for handling such scenarios.
-
UDP Reliance: While UDP offers advantages in terms of speed and efficiency, it also introduces potential issues such as packet loss or out-of-order delivery. TFTP’s reliance on UDP means that it may not be the best choice for environments where reliability is paramount, particularly over unreliable or congested networks.
Most commom use cases of TFTP
- Network Booting: Booting diskless devices over a network, where the operating system is loaded from a remote server.
- Firmware Updates: Updating firmware on network devices, such as routers, switches, and printers.
- Configuration Management: Transferring configuration files to network devices for provisioning and management.
- Software Distribution: Distributing small files, such as firmware updates or configuration files, across a network.
Conclusion
In conclusion, TFTP has established itself as a valuable tool within network environments. Its core strengths lie in simplicity, speed, and minimal resource requirements. These attributes make TFTP particularly well-suited for tasks like network booting, firmware updates, and configuration management, especially for devices with limited processing power or memory. While more feature-rich protocols exist for broader file transfer needs, TFTP remains a relevant and efficient solution for specific use cases.
Question
How do you think TFTP compares to other file transfer protocols in terms of ease of use?




